How Does A Non-Custodial Wallet Secure Assets?
you are solely responsible for your wallet security while using non-custodial wallets, as the onus to keep your private key safe is on you, and no service provider can do that for you.

Non-custodial wallets stand out as cryptocurrency wallets that empower users with absolute control and ownership of their private keys. Unlike custodial wallets, non-custodial wallets aren't protected or managed by any provider; they are fully decentralized, transferring the responsibility of securing and managing assets to each user.
With the growing prevalence of cryptocurrencies as investments and as means for fund transfers, knowing how these assets are safeguarded is paramount. As digital finance expands, the risks of fraud, unauthorized access, and cyber threats are on the rise.
So, understanding how non-custodial wallets function and how safe they are can help you, as a user, make informed decisions about securing your digital wealth.
What are Non-Custodial Wallets?
Digital wallets that allow customers total ownership and management over their private keys are known as non-custodial wallets. Non-custodial wallets do not rely on outside parties to maintain or secure the cryptographic keys connected to the user's digital assets, unlike custodial wallets or conventional bank accounts.
The user creates, keeps, and safeguards their private keys in a non-custodial wallet. Private keys are essential cryptographic codes that provide access to the money kept in the blockchain wallet. Because of this decentralized method, users are less reliant on third-party providers to manage and secure their cryptocurrency investments and have more liberty.
Decentralization is a fundamental characteristic of non-custodial wallets that distinguishes them from custodial alternatives. Because it is decentralized, there is no longer a requirement for a single point of control, which lowers the possibility of vulnerabilities or systemic breakdowns. Assisting consumers with a transparent, peer-to-peer, and tamper-resistant environment for their digital assets is consistent with the fundamental principles of blockchain technology.
There are several types of non-custodial wallets, such as paper, hardware, and software. Users can select the type of solution that best suits their needs and tastes from the various options available, each offering varying degrees of accessibility, convenience, and security.
How Do Non-Custodial Wallets Secure Assets?
Private Key Ownership
One of the cornerstone features of non-custodial wallets is the concept of private key ownership, which allows users to have exclusive control over their cryptographic keys.
Private key ownership ensures that individuals are not reliant on external parties, enhancing the security and privacy of their holdings. This autonomy over private keys empowers users to manage their assets independently, reducing the risk associated with third-party vulnerabilities.
This private key is typically encrypted in lengthy digits that are difficult to memorize or even write down; however, non-custodial wallets usually provide a decrypted, human-readable form of the private keys in the form of seed phrases (usually consisting of 12–24 words) and are used to recover or restore the wallet when necessary.
User Control and Autonomy
Non-custodial wallets prioritize user control and autonomy, allowing individuals to decide independently on their cryptocurrency holdings. Users can initiate transactions, manage portfolios, and choose preferred security measures.
This level of control fosters a sense of ownership and responsibility as users become active participants in securing and overseeing their financial assets. The emphasis on user autonomy aligns with the decentralized ethos of cryptocurrencies, offering a departure from traditional financial systems that often involve intermediaries and centralized control.
Encryption
Security in non-custodial wallets is significantly reinforced through robust encryption protocols and recovery phrases. These cryptographic techniques serve as a protective layer, safeguarding sensitive information, including private keys and transaction data.
State-of-the-art encryption algorithms, such as AES (Advanced Encryption Standard), are commonly employed to secure the communication and storage of data within the wallet. Encryption ensures that the data remains indecipherable without the proper cryptographic keys, even if unauthorized access is attempted. Implementing strong encryption protocols is fundamental to creating a secure environment for users' digital assets, minimizing the risk of data breaches and unauthorized access.
How To Set Up Non-Custodial Wallets on Cwallet
Cwallet provides both custodial and non-custodial wallet solutions for its users.
Custodial wallet options are good for beginners that aren't very familiar with crypto wallets and security; however, if you prefer a non-custodial wallet, it's quite easy to set up.
All you need to do is to Download and install Cwallet on your device. Upon launching it, you'd be presented with the Custodial wallet option by default, from which you can switch to the Non-Custodial wallet with a single button switch, as shown below.
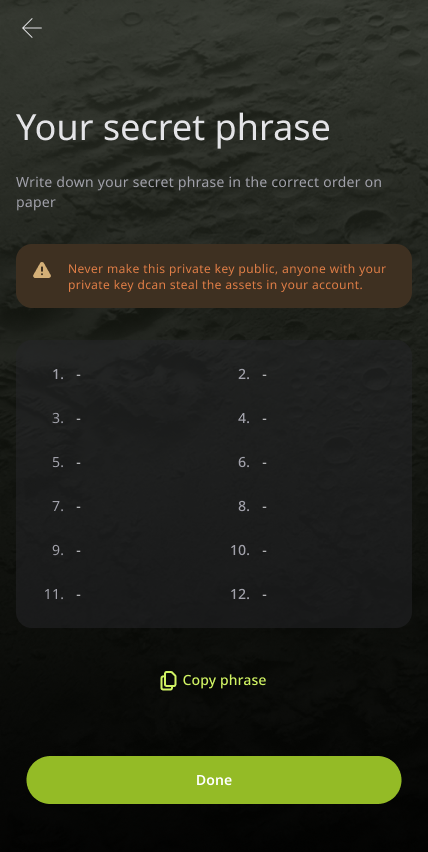
Then, from the non-custodial wallet, you can create a new wallet; you'll be given a secret recovery phrase to secure your private keys, which you can back up, and then your new wallet is set to use.
Regardless of the non-custodial wallet you use, it is important to know that you are solely responsible for your wallet security while using non-custodial wallets, as the onus to keep your private key safe is on you, and no service provider can do that for you.
End Note
Indeed, you can take charge of your crypto assets with non-custodial wallets thanks to their decentralized nature. However, for a beginner, you may find the security protocols of non-custodial wallets quite challenging. There are no email addresses or passwords, as you are previously used to, and if you lose your seed phrase, no one can recover your wallet.
With great power comes great responsibility, so if you are considering the possibilities of a non-custodial wallet, download Cwallet. Beyond facilitating secure and encrypted transactions, Cwallet also provides a user-friendly interface for creating and managing non-custodial wallets.
With Cwallet, you can experience the advantages of decentralized control and robust security protocols, contributing to a safer and more empowering digital asset management experience.